Reported by Lucy Colback
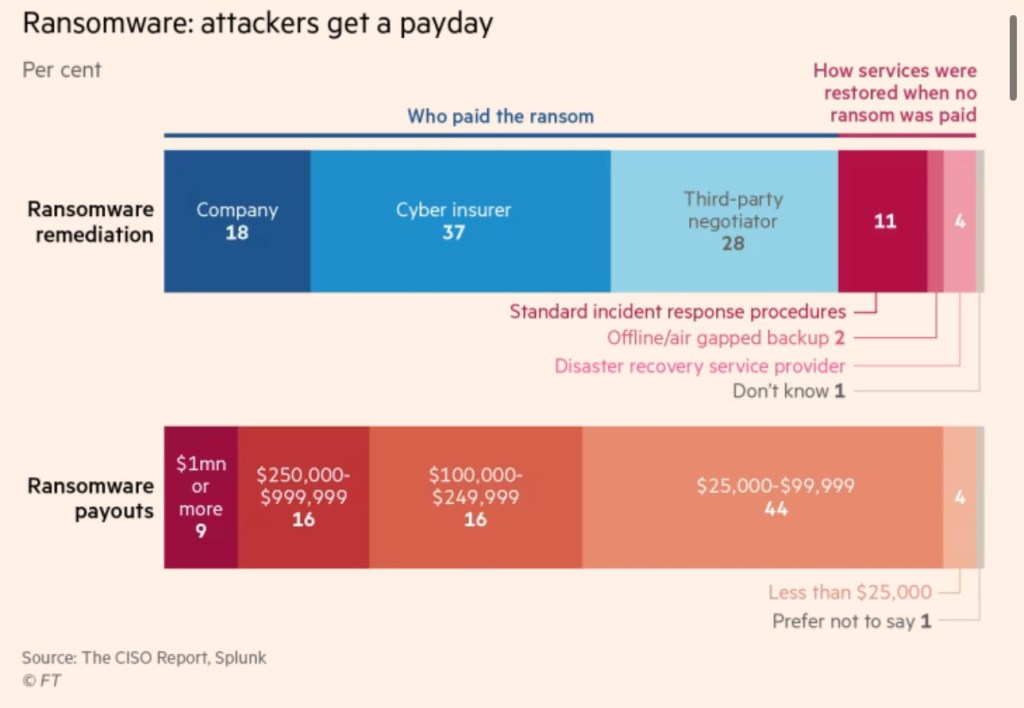
Stick ’em up
Ransomware is a ubiquitous problem. In a traditional ransomware attack, in which files are encrypted and users’ access disabled, “you have between 45 seconds and four hours before your entire network is done”, says Mick Baccio, global security adviser at Splunk, a cyber security company.
One UK/US crime group, Scattered Spider, has achieved infamy for its ransomware attacks on Caesars Entertainment and MGM Resorts International.
In February 2024 Chainalysis, a blockchain data platform, said known ransomware payments in 2023 exceeded $1bn, a new high after a respite in 2022. Given the difficulty in tracking all incidents, this is probably a conservative figure. The incidence of “big game hunting” — where targets have a high value or high profile or both — has also risen. Ransoms greater than $1mn have increased as a share of the total volume of payments.
No one is immune. In the 12 months to June 2024, headline victims of ransomware included ICBC, the Chinese bank; New York state, the government body, at a key point in its budget process, and Allen & Overy, the London law firm.
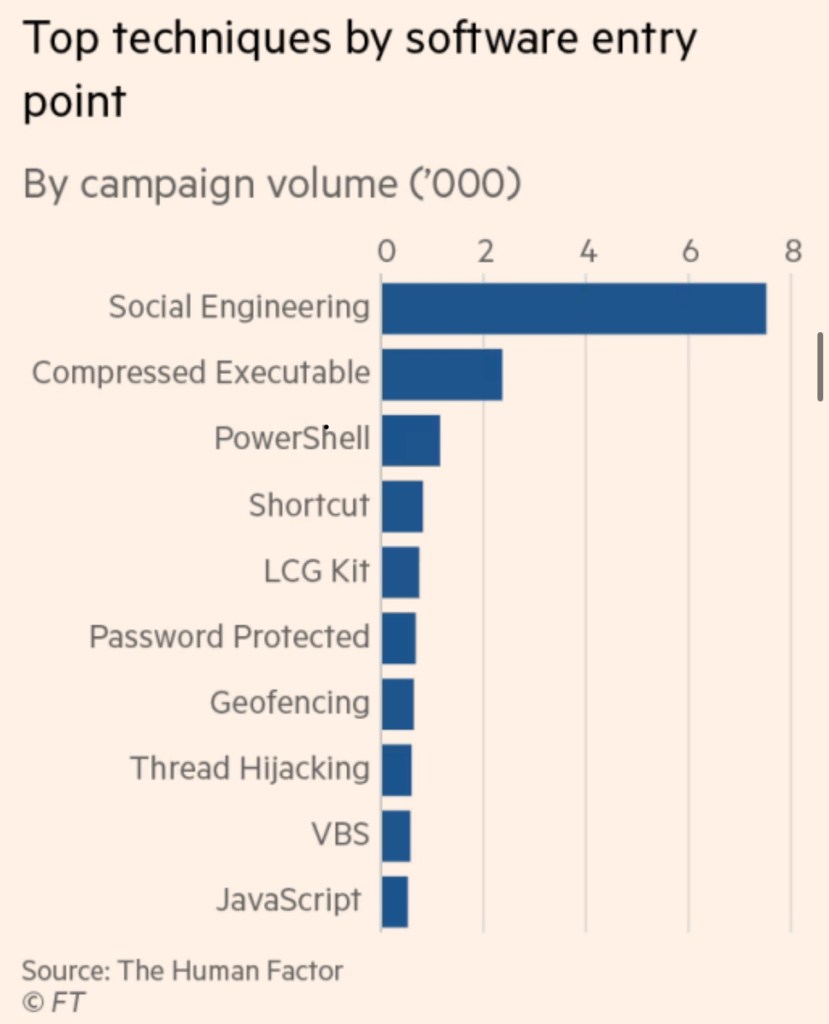
Social climbing
Social engineering — the art of manipulating people into giving up entry keys, passwords or other entry data — is a common way to gain access to a system. It began with the rudimentary “help me” scam emails or “reset your password” phishing mails but is now far more sophisticated. Today it can involve elaborate “pretexting”, where scammers create a plausible story to lure the unwary into handing over keys.
Verizon says half of all social engineering attacks involve criminals compromising business email, which is the second most-common entry point after web applications. Such attacks doubled from 2022 to 2023. In the fourth quarter of 2023, Mimecast found that file-sharing links purporting to be from legitimate providers such as Evernote were frequently used in attempted attacks. Phishing for SME businesses’ entry credentials to cloud services is common.
The cost to business is considerable. The FBI says that between 2013 and 2022, the cumulative loss from compromised email was $50bn. Of this, more than 136,000 US-based victims reported a total of $17bn losses to the FBI’s Internet Crime Complaint Center (IC3).
AI is adding to the criminals’ toolbox. Not only does it make phishing for email content more fluent (in English, at least), it has led to more sophisticated ploys. Sumsub, the verification software provider, points to a 700 per cent increase in deepfake incidents in the fintech sector between 2022 and 2023 and a tenfold increase across all industries. Crypto and fintech cases accounted for 96 per cent of these.
Read full report: https://www.ft.com/content/8a79ab25-c902-4110-bcb8-be2fd422f6bf
